Yasuoka's hack log
[ 2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 ]
2011-12-27
- pf の DoS mitigation については、 http://www.openbsdsupport.com.ar/books/nuevos/OpenBSD%20&%20PF%20Robust%20firewalls.pdf がわかりやすい
2011-12-26
- uim-fep を anthy で使う場合に、文節を縮める方法がずっとわからなかったが、この話は、 http://code.google.com/p/uim-doc-ja/wiki/UimFep#%e3%82%ad%e3%83%bc で解説されていた
- 端末として ctrl-i は <Tab> と区別がつかないのが原因らしい
- uim-pref-gtk を起動して「Anthy キー設定1」タブの「文節を縮める」に "tab" を追加するることで、 Ctrl + i で文節縮めることができるようになる
2011-12-24
- VAIO の HDD 引越し終了。最終的に
Filesystem Size Used Avail Capacity Mounted on /dev/wd0a 1005M 143M 812M 15% / mfs:15305 124M 150K 118M 0% /tmp /dev/wd0e 9.8G 372M 9.0G 4% /var /dev/wd0f 2.0G 527M 1.4G 28% /usr /dev/wd0g 1005M 182M 773M 19% /usr/X11R6 /dev/wd0h 9.5G 1.5G 7.5G 17% /usr/local /dev/sd2a 148G 42.4G 98.1G 30% /home /dev/wd0l 98.4G 13.4G 80.1G 14% /source /dev/sd1a 19.7G 8.9M 18.7G 0% /home/yasuoka/iij
- /home と /home/yasuoka/iij は softraid(4) の crypto descipline を使って暗号化している。 crypto descipline なディスクを起動時に認識させる方法は無いようなので、 /home は /etc/rc.local で
bioctl -l /dev/wd0n -c C softraid0 && fsck -p /home && mount /home
- としている。~/iij は、移動中は unmount しておきたいので、必要なときに
% sudo sh ~/iij.sh mount *** bioctl -l wd0m -c C softraid0 Passphrase: (パスフレーズを入力) *** fsck -p /home/yasuoka/iij /dev/sd1a (17f5d2522e5dce62.a): file system is clean; not checking *** mount /home/yasuoka/iij OK %
- というようなスクリプトでマウントし、/etc/apm/{suspend,standby} にて、アンマウントしている。
2011-12-23
- さすが歌代さん https://twitter.com/#!/uta46/status/149873072197996546
- ノートパソコンの HDD 換装。手が滑って、VAIO の特殊な SATA ケーブルをちぎってしまうトラブルがあったりしたが、ようやく引越も終わりつつある
% dmesg | grep wd0 wd0 at pciide1 channel 0 drive 0: <Hitachi HTS547575A9E384> wd0: 16-sector PIO, LBA48, 715404MB, 1465149168 sectors wd0(pciide1:0:0): using PIO mode 4, Ultra-DMA mode 6 root on wd0a (5ecc213ba70e75a7.a) swap on wd0b dump on wd0b % % df -h Filesystem Size Used Avail Capacity Mounted on /dev/wd0a 1005M 152M 803M 16% / /dev/wd0e 9.8G 375M 9.0G 4% /var /dev/wd0f 2.0G 527M 1.4G 28% /usr /dev/wd0g 1005M 182M 773M 19% /usr/X11R6 /dev/wd0h 9.5G 1.5G 7.5G 16% /usr/local /dev/sd0d 73.5G 63.9G 5.9G 91% /home %
- 残すは /home だけ。softraid 使って暗号化する予定
2011-12-21
- いまだに mew の検索機能を使っていなかったのだが、ようやくインストールして使ってみた。
- env PKG_PATH=ftp://ftp.iij.ad.jp/pub/OpenBSD/5.0/packages/i386/ sudo pkg_add hyperestraier して、Hyper Estraier のインストールは終了
- mew の summary モードで kM すると全フォルダのインデックスが作成される
- k? k/ とかで、検索できるようになる。こんなに簡単だったのか!
2011-12-13
- 端末は OpenBSD 標準の xterm に、k14 を iso10646 変換したフォント http://www.ie.u-ryukyu.ac.jp/~kono/pub/software/ を指定して使っているが、w3m が漢字に対し bold を使おうとすると化ける。bold で選択するフォントに、漢字がないからか
- iso10646 な k14 はそれなりのユーザがいると思うので、Linux や FreeBSD の package を漁ると、ヒントがあるかもしれない
- ~/ の disk usage が 100% になっていて焦った。ついでに softraid(4) で暗号化するなどの計画があるので、2.5" HDD 発注することにした
2011-12-12
- BROTHER の Linux 向け情報のページは、 ここ にある
- HL-1850 を USB 接続で使おうとしているがうまく動いていない
2011-12-05
- マウスパッドでのタップの問題は、mpi@ さんに助けてもらった結果、以下の設定を /etc/X11/xorg.conf に加えることで解決することがわかった
Section "InputClass"
Identifier "Touchpad defaults"
MatchIsTouchpad "on"
Option "TapButton1" "1"
- 残った問題として "Tap and Drag" が効かない場合が多い気がするけど、これは pms に ALPS 対応が入る前からだった気がするのでしばらく使って様子をみる
2011-11-28
- 勤務先で Xerox の ApeosPort-III C4405 を使っていて、このプリンタは Xerox のサイトから適当な PPD ファイルをダウンロードして CUPS で利用すれば使えるようになる
- 当初、まったく問題がなかったのだが、いつの間にか (CUPS をアップグレードしたら?) プリンタオプションで設定項目の文字が表示されない問題が発生するようになっていた
- 試行錯誤した結果、PPD ファイルの LanguageEncoding が JIS83-RKSJ となっているのが問題の原因となっていることがわかった
- PPDファイルを UTF-8 に変換し LanguageEncoding を UTF-8 と書き換えることで問題を回避できる
- OpenBSD の locale は charset 変換をサポートしないので、UTF-8 以外で漢字等を用いることができない。なので、LanguageEncoding の問題は OpenBSD だけの問題かもしれない
2011-11-21
- US キーボードで X を使っている場合の rdesktop のキーマップ調整を ぺちぱーのユウウツ - Gnome-RDPを使う を参考に行った
% mkdir ~/.rdesktop/keymaps/ % cp /usr/local/share/rdesktop/keymaps/en-us ~/.rdesktop/keymaps/ % cat >> ~/.rdesktop/keymaps/ map 0xe0010411 Kanji 0x29 Alt_R 0x38 % rdesktop -k ja-us
2011-11-17
- virtio。FreeBSD のこっちも良さげ
2011-11-16
- virtio-2011_11_16.diff 更新
- 2011-11-14 のアイコンバグは oga さんが直していた。さすが。
- あとは VAIO のマウスパッドでタップができない問題もある。
- tap できないのは synaptics(4) のデフォルトという説明を受けたが、 synaptics って何状態なので、まずは勉強から...
2011-11-14
- 最新の snapshot に入れ替えたら、Ctrl-Alt-F1 〜 Ctrl-Alt-F4 が効かなくなった
- pkg_add -u したら、gtk-pixbuf を使ったアイコンなどの色が化けている模様。背景色が黒になっている? ただし、xdm からログインした場合のみに再現し、xinit の場合には再現しない。
2011-11-12
- BUFFALO WLI-UC-GNM は run(4) で認識する
run0 at uhub0 port 1 "Ralink 802.11 n WLAN" rev 2.00/1.01 addr 2 run0: MAC/BBP RT3070 (rev 0x0201), RF RT3020 (MIMO 1T1R), address 4c:e6:XX:XX:XX:XX
- WEP なしでは使えるが、WEP 40bit key では使えないっぽい。受信はできているが送信がダメ
2011-11-08
- NetBSD には入っている syslogp(3) には、まだマニュアルがない?
- ↓のような場合、横スクロールバーを表示するようにしたい...
- relayd が落ちてた
Nov 6 23:44:16 stm0 relayd_yasuoka[25298]: fatal: relay_dispatch_parent: imsg_read error: Message too long
2011-11-05
- virtio はカーネルデベロッパに人気がありそうだから、僕が hack する必要はないな。ということで、作業中断して様子見。
- そうこうしているうちに NetBSD には commit されてた。 http://mail-index.netbsd.org/source-changes/2011/10/30/msg028443.html
2011-10-28
- virio の資料
- Virtio: Towards a De-Fact Standard For Virtual I/O Devices by Rusty Russell @ IBM OzLabs
- Virtio PCI Card Specification
2011-10-26
- virtio-2011_10_26.diff 更新
- 同一 vlan に 2 本の vioif を差し、片方だけリンクアップさせておくと、受信がおかしくなる。qemu のバグか、OpenBSD tun を tap する時の仕様っぽく、いずれにしても virtio ドライバの不具合ではないと思われるのでスルー。
2011-10-24
- OpenBSD の vi ってなんで $HOME/.exrc 読み込まないんだろう (2012-02-08 に解決)
2011-10-22
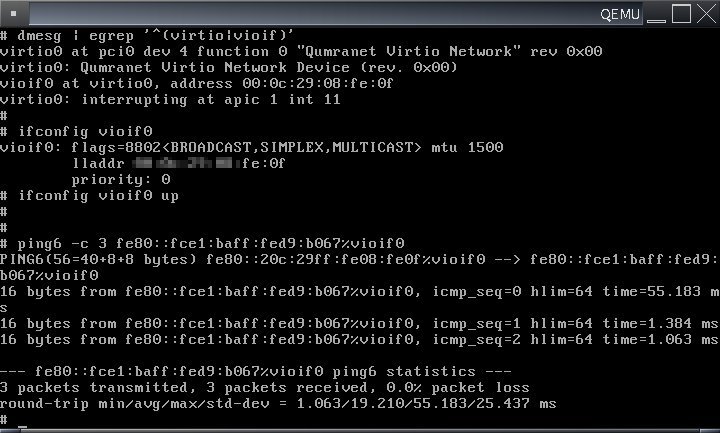
- http://www.minoura.org/~minoura/virtio-100605/ を OpenBSD に移植してみた。virtio というバスの上に viomb vioif デバイスが載るが、とりあえず virtio だけ。 virtio-2011_10_22.diff
2011-10-21
- トヨタでは、「カタログエンジニア」と呼ぶのか。 トヨタ生産方式@Wikipedia
2011-10-19
- L2TP/IPsec の場合には、trasport mode で、かつ、Phase-2 ID を限定するポリシーが書けるべきだ。(けど現在の実装では書けないと思われるので、書けるようにする必要がある)
2011-10-17
- L2TP/IPsec の場合、特定多数が秘密鍵を共有するので、その鍵で認証した対向が提案する任意の IPsec SA を確立するのは危険。次のように isakmpd.policy を設定すれば、transport mode に限定できる
Authorizer: "POLICY"
Conditions: app_domain == "IPsec policy" -> "false";
Authorizer: "POLICY"
Licensees: "passphrase:PRESHARED-KEY"
Conditions: app_domain == "IPsec policy" && esp_encapsulation == "transport"
-> "true";
2011-10-15
- http://marc.info/?l=openbsd-cvs&m=131837666003954&w=2 は、最終行にゴミが入っているし、その次の http://marc.info/?l=openbsd-cvs&m=131914643424548&w=2 は "ok " を忘れたし、その次 http://marc.info/?l=openbsd-cvs&m=131914643624603&w=2 は、IPsec が IPesc になっている。ケアレスミスが多くて恥ずかしい
- marc.info 更新されん、と思ったら、サーバトラブってるのね http://marc.info/?q=news
2011-10-13
- pppoe(8) のパッチが送られてくることが多いので、自分でも使おうと思う
2011-10-12
- uim-fep が CPU 100% になったり、tmux 内で文字の表示が欠けたりする。操作になれてないという面もあるかもしれないが、わりとイライラする
- 開発元 http://code.google.com/p/uim-doc-ja/ はそれなりにアクティブな感じなので、デバッグ体制整えて直していこうと思う
2011-10-10
- openbsd の cvs と同期, svn 変換, 自動ビルドまでを自動化した
2011-10-05
- OpenVPN とソースコードレベルで格闘。OpenVPN って、想像以上にカオス。
2011-10-03
- klips-ng in openswan 2.6.x: http://lists.openswan.org/pipermail/users/2009-June/016886.html
2011-10-01
- http://hibari.2ch.net/test/read.cgi/unix/1278782251/163 wsconsctl いけると思うんだけど。
- http://www.oxide.org/cvs/yasuoka.html
2011-09-30
- sys/mbuf.h に XXX が残してあったの忘れてた
453 #define PACKET_TAG_PIPEX 0x0400 /* pipex context XXX */
2011-09-29
- isakmpd のタイマー管理は gettimeofday を使っている。clock_gettime に 置き換えるべきなので、TODO に入れとく
- NPPPD/L2TP IPsec problems (http://marc.info/?l=openbsd-misc&m=131704339405331&w=2 ) の問題は二つで、
- Windows が Identifier Type として FQDN で通知してくるが、isakmpd では、 それを未実装として、拒否している
- UDP の checksum が一致せずに drop.
2011-09-28
- github に移動したらしい https://github.com/openbsd/flashboot/
2011-09-27
- このサイトの構成を変更した関係で、google の「印刷 カレンダー」のランクが 22 位ぐらいまで落ちたけど、今見たら 1 位に復活してた。ページ構成変更は wiki.c のとおり 302 でやったが、Google 対策としては、これは何点な んだんろうか。
- NPPPD/L2TP IPsec problems (http://marc.info/?l=openbsd-misc&m=131704339405331&w=2 ) IPsec NAT-T との組み合わせは、未調整なので、まぁいろいろとあるでしょう。
- Systrace Sandboxed OpenSSH
- jail 内でさらにシステムコール (socket() とか) などを制限
2011-09-22
- 自宅サーバ: 安定したと思っていいかな?
$ uptime 3:16AM up 30 days, 18 mins, 2 users, load averages: 0.14, 0.11, 0.09
2011-09-21
- 5.1 こそは。"npppd & OpenBSD 5.0" http://marc.info/?l=openbsd-misc&m=131652335129938&w=2
- calendar.html は、祝日計算は某音楽配信サイト用に作成した自前の Java 実装を使っていて、カレンダーの描画は、PDF は Illustrator で作成したものを脳内で PDF-J に変換して書いている。apache fop を使って servlet で書き直せるので、いつかそうしたい。
- 今時は、HTML の canvas に書いて、canvas から PDF への変換はブラウザ次第ということでいいのか。(2011-09-27 追記)
2011-09-19
- bioctl(4) に "Use of the CRYPTO & RAID 4/5 disciplines are currently considered experimental." と書いてある。CRYPTO 使おうと思ってたんだけど、どうしようか。